Comprehensive protection against hacking attempts for the most high-load web applications with minimum delays and guaranteed service availability
Service Level Agreement for availability of customers' applications
Effective tools for false-positives protection
Bandwidth over 4 Tbps
Despite their importance, often it’s web applications which are the ‘weak link’ within organizations’ security perimeters. Typically, companies’ in-house web applications have complex architectures and many borrowed components, and in-house developers do not have enough time to organize the proper security for these resources. The application security is sometimes a sacrifice in the run for future releases of new features or functionality. Web applications are subject to various threats, such as theft of confidential data, fraud, or spoofing, and serve as a convenient entry point for further attacks.
Your Critical Web Resources are under Control
Strengthen Your Protection
Qrator.WAF is an advanced next-generation tool that helps to prevent a wide range of threats to web applications during their operation.
Full Coverage
A high level of protection against both simple and complex targeted attacks is achieved by using the most detailed models of the protected application along with signature-based and behavioral anomaly detection methods.
Always Stay Online
The distributed infrastructure of WAF filtering nodes within the perimeter of the Qrator Labs network allows you to protect even the most heavily loaded applications with minimal delay and guaranteed service availability.
Major classes of web threats, including OWASP Top 10
Brute force attacks
Attacks on identification and authorization mechanisms
API security
Corporate service security
Basic security mechanism
Enhanced security capabilities
HTTP protocol validation (request types, headers, and their parameters, etc.)
Automatic filtering of static resources: a separate mode for processing static resources (provides ease of data analysis in the control and monitoring subsystem)
Analysis of requests and responses using signature analysis (including those that detect OWASP Top 10 attacks)
The mechanism of "black" and "white" lists for basic types of sources (IP address, URLs)
Blocking sources when multiple anomalies are detected in the requests
Limiting the rate of requests from one source (Rate Limiting) for the application as a whole.
Automatic detection of the performed logical actions and checking its parameters for compliance with the predetermined patterns
Controlling sequences of logical actions
Success measurement of the performed actions based on the analysis of responses, including nested data
Defining sources that are arbitrary parameters of logical actions that characterize the request source (IP address, session ID, user name, certain cookie, etc.)
Controlling users and sessions, which define the key session parameters and the logical actions that are used as a framework to set, monitor, and disable these parameters)
Controlling user authorization at the level of sessions and performed logical actions
Controlling the rate of requests to individual logical actions depending on the parameters of the request source and other parameters (Rate Limiting)
No need to have special expertise to make changes to the architecture of the protected application and configure cloud WAF rules. We provide access to a ready-made solution based on the customer's wishes and provide round-the-clock monitoring of incidents in your personal account with the following features available
Summary
Events
Transactions
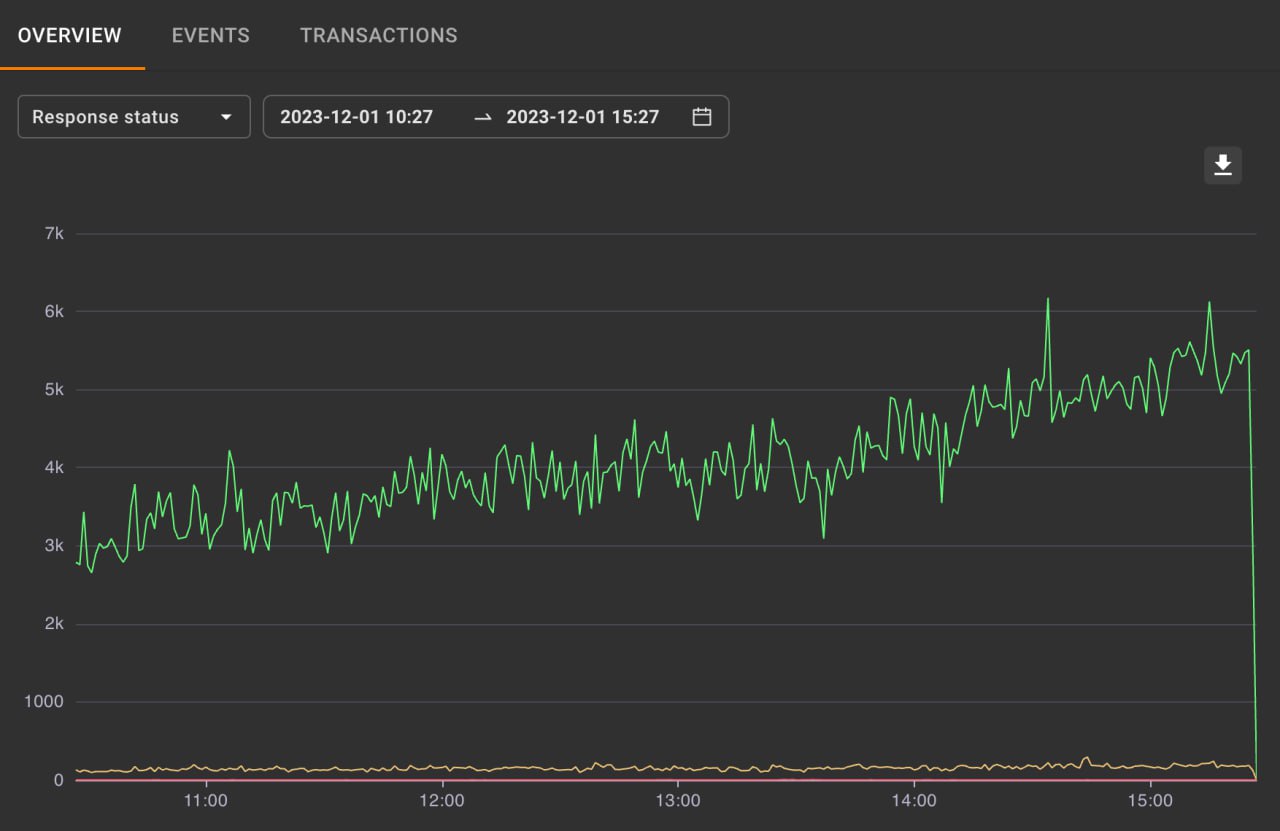
A dashboard with different metrics of the protected web applications traffic (response code, locks, delay, sessions, hostility).
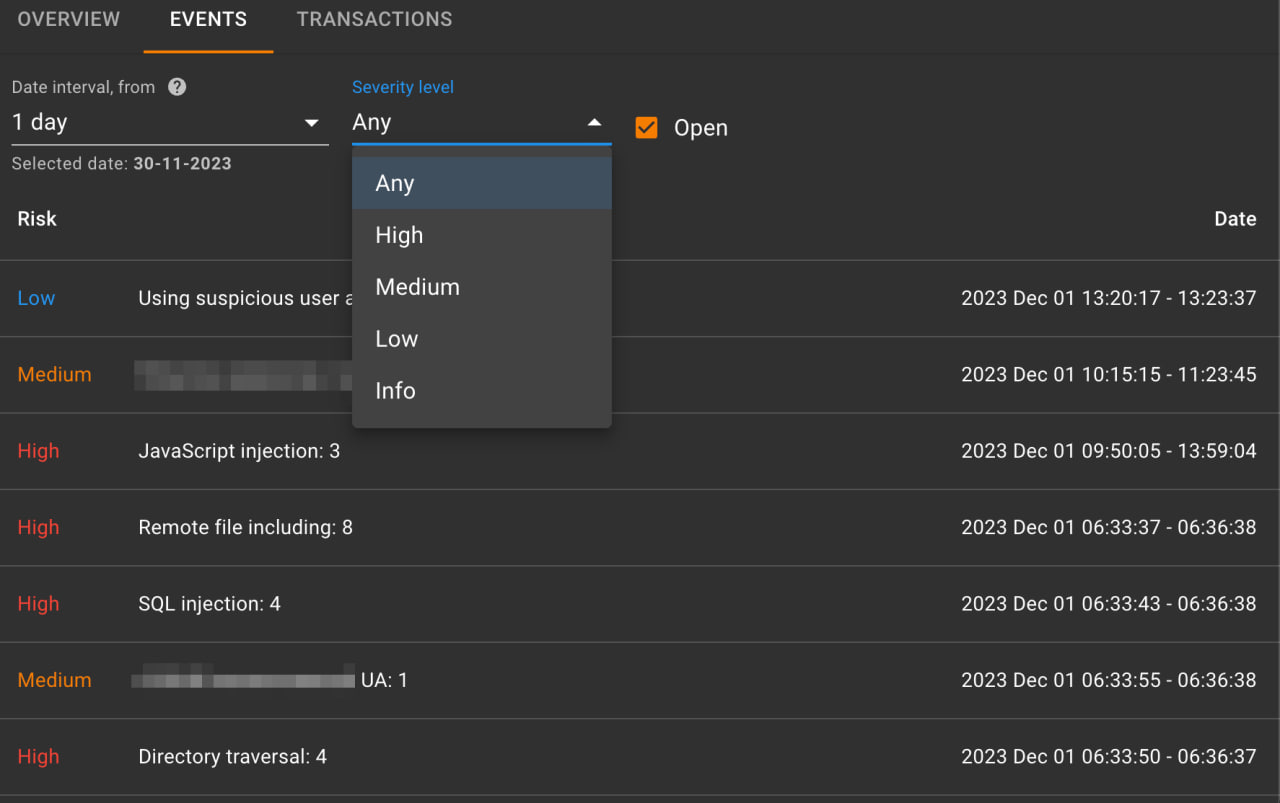
A flexible tool for analyzing detected security events, grouped by type and threat level, with an option to view all the details of each individual transaction. It is also possible to manually suppress a false positive when a false positive lock is detected in the transactions.
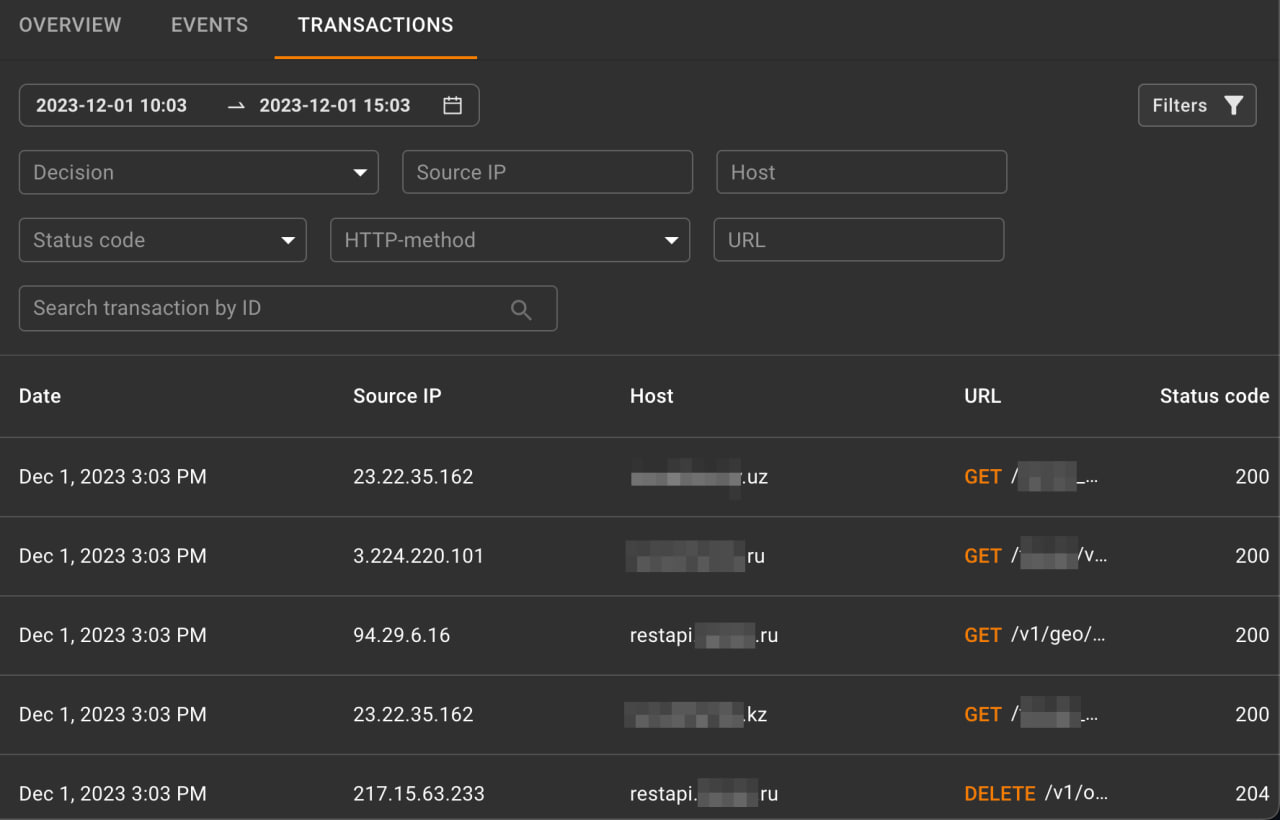
A section where all transactions of the protected application are stored, offering the possibility to flexibly search for requests using various parameters.
Backspace Technologies - Wholesale VOICE and APN solutions provider - improves real-time BGP anomalies detection to ensure better network performance and high availability of service with Qrator.Radar.
Qrator.Radar helps Dailymotion - Online video sharing platform - ensure high quality of video broadcasts with a primary focus on controlling and detecting network anomalies, which may cause a degradation of the video delivery service.
Cindicator - Crypto trading company - stops Denial of Service issues and mitigates infrastructural and reputational risks with Qrator Labs filtering network letting the platform run like clockwork 24/7.
Olymp Trade - Online trading company - reaches continuous availability of its resources and provides a secure trading environment for customers using Qrator.AntiDDoS solution
Qrator Labs helps Lazada - Ecommerce company - prevent targeted attempts to disable the system with sophisticated DDoS attacks ensuring uninterrupted business operations, and boosting website performance.

The Arab International Cybersecurity Conference & Exhibition shields against potential network attacks with Qrator.AntiDDoS and WAF solutions
A Web Application Firewall (WAF) protects web applications from hacking attempts, fraud, and data theft. It analyzes traffic, blocks malicious requests, and ensures applications remain secure and available — even under heavy load or targeted attacks.
Unlike network firewalls that protect infrastructure at lower layers (L3/L4), Qrator.WAF operates at the application layer (L7). It uses signature-based detection, semantic anomaly detection, and business logic analysis to stop complex attacks that bypass standard firewalls.
Qrator.WAF provides comprehensive protection against:
No. Qrator.WAF is built on a distributed cloud infrastructure with 4+ Tbps network capacity. Filtering nodes operate with minimal latency, ensuring that applications stay fast and available while being protected.
Qrator.WAF uses machine learning and early suppression mechanisms to minimize false positives. This ensures legitimate user traffic is not blocked, while security operators can focus only on real threats.
Yes. Qrator.WAF creates detailed models of your applications, learns from user behavior, and adapts to specific business logic. This allows highly customized protection for complex and in-house developed applications.
Yes. Qrator.WAF protects APIs by validating requests, limiting abnormal traffic rates, and blocking unauthorized or suspicious access attempts. This is critical for businesses relying on microservices and API-driven architectures.
Deployment is fast and seamless. Since Qrator.WAF is a cloud solution, it requires no changes to your internal infrastructure. Setup can be completed within minutes, and protection begins immediately.
Customers have access to a real-time monitoring dashboard showing key metrics such as response codes, attack events, session details, anomalies, and blocking activity. This transparency ensures full visibility of application traffic.
Qrator provides a 99.95% SLA for application availability. This high standard is backed by contract — if uptime is not met, compensation applies.
Yes. A 7-day free trial and live demo are available, allowing businesses to evaluate performance, integration, and security benefits before making a long-term commitment.