Understanding BGP Hijackin
BGP hijacking is the redirection of Internet traffic caused by an illegitimate BGP announcement from a malicious or misconfigured autonomous system (AS). In essence, the offending AS either intentionally or unintentionally reroutes traffic meant for other destinations through its own network.
BGP hijacking incidents can result in the interception of sensitive data, the redirection of users to malicious websites, data loss, service disruptions, and other serious issues. The fundamental flaw that makes BGP hijacking possible is the trust-based nature of the Border Gateway Protocol (BGP), which forms the backbone of the modern Internet.
What is Border Gateway Protocol (BGP)?
Border Gateway Protocol (BGP) is the Internet’s routing protocol, that enables autonomous systems to exchange information about the most efficient data paths from one AS to another. Similar to a ZIP-code system, BGP helps direct traffic across the Internet, continuously optimizing routes based on network conditions.
BGP Hijacking: How Malicious Route Announcements Threaten Internet Security and Stabilit
BGP hijacking is the redirection of Internet traffic caused by an illegitimate BGP announcement from a malicious or misconfigured autonomous system (AS). In essence, the offending AS either intentionally or unintentionally reroutes traffic meant for other destinations through its own network, leading to serious cybersecurity risks.
BGP hijacking incidents can result in the interception of sensitive data, the redirection of users to malicious websites, data loss, service disruptions, and other serious issues. The fundamental flaw that makes BGP hijacking possible is the trust-based nature of the Border Gateway Protocol (BGP), which forms the backbone of the modern Internet.
What is Border Gateway Protocol (BGP)
Border Gateway Protocol (BGP) is the Internet’s routing protocol, that enables autonomous systems to exchange information about the most efficient data paths from one AS to another. Similar to a ZIP-code system, BGP helps direct traffic across the Internet, continuously optimizing routes based on network conditions and routing efficiency.
An Autonomous System (AS) is a collection of IP networks managed by a single authority under a unified routing policy. Examples of ASes include large Internet service providers (ISPs) and networks belonging to major organisations, such as corporations, universities, and government agencies. Each AS is identified by a unique Autonomous System Number (ASN), which is used in BGP routing to exchange information with other autonomous systems across the Internet.
The modern Internet infrastructure consists of tens of thousands of autonomous systems interconnected in a complex, mesh-like structure. Finding the most efficient path from one AS to another would be impossible without a protocol like BGP, making it essential to the Internet’s operation.
How BGP Hijacking Works
BGP hijacking occurs when an autonomous system (AS) announces false or illegitimate routes, misleading other ASes into directing Internet traffic through it. This can happen unintentionally, due to misconfiguration, or with malicious intent. The mechanics of such incidents generally boil down to two basic scenarios:
- Shorter path announcement: BGP prioritizes routes based on the shortest available path. In this scenario, the offending AS falsely announces a shorter route to a specific range of IP addresses than any existing route. Neighboring ASes, trusting the announcement, redirect traffic through the hijacker’s AS.
- More specific path announcement: BGP also prioritizes more specific IP address ranges over broader ones. If the hijacking AS announces a smaller IP range than the legitimate AS, this route is preferred, and traffic is directed through the hijacker’s AS.
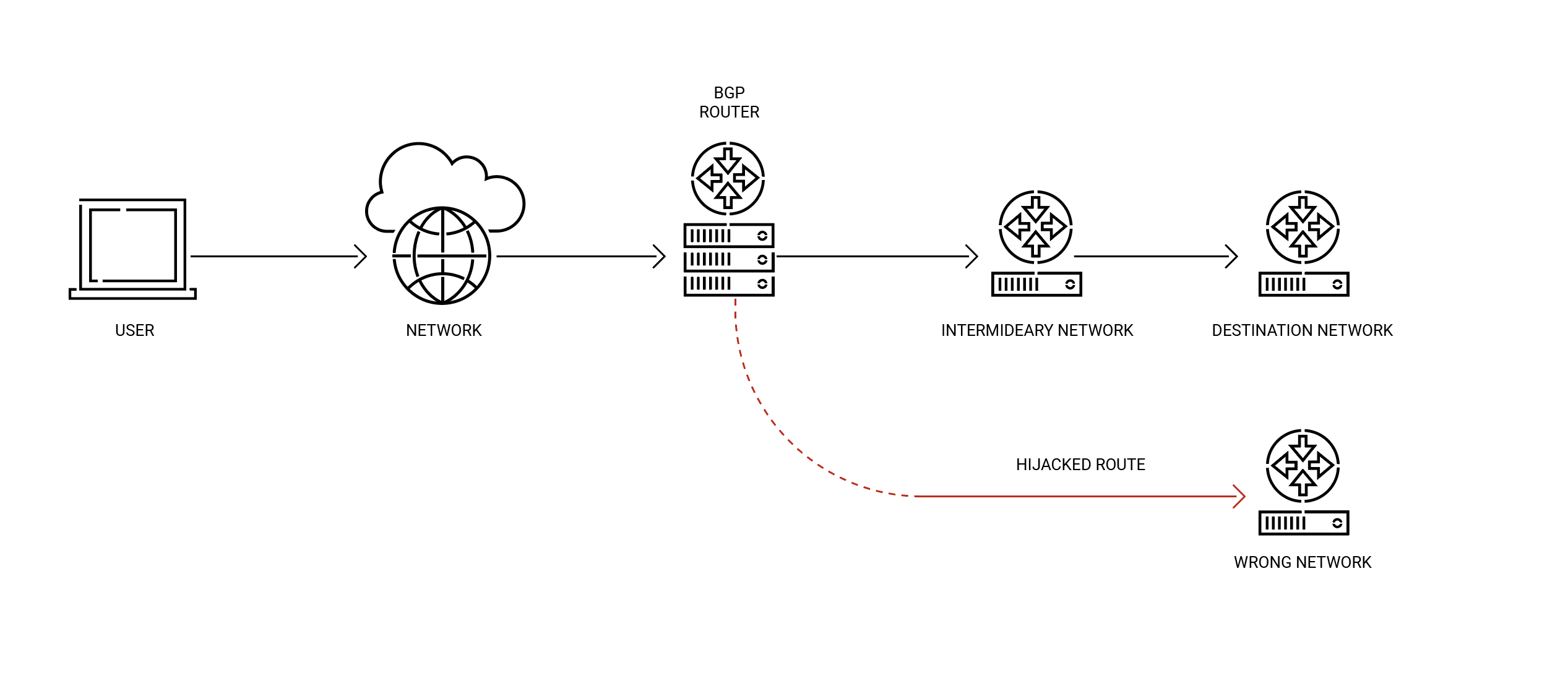
Both scenarios exploit the lack of validation in the Border Gateway Protocol (BGP), making BGP hijacking a serious threat to network security and stability. By default, BGP operates on trust, accepting route announcements without verification. This allows malicious or misconfigured ASes to introduce false routes.
Consequences of BGP Hijackin
BGP hijacking can lead to a wide range of consequences, with severity ranging from moderate to critical, depending on the nature of the attack and the targeted systems. Here’s a breakdown of some of the most common outcomes:
- Increased latency: When traffic is rerouted through an unintended path, it can significantly increase the time it takes for data to reach its destination. This can lead to slow loading times, degraded performance for critical online services, and a poor user experience, especially for real-time applications like video conferencing, online gaming, or financial trading.
- Blackholing: BGP hijacking can result in “blackholing,” where traffic is dropped before it reaches its intended destination. This can cause partial or complete service outages, as users are unable to access websites or online services, effectively making them unreachable.
- Traffic monitoring: BGP hijacking can be used for passive attacks where traffic is rerouted through the attacker’s network without the users' knowledge. This allows the attacker to monitor and analyze sensitive data, potentially gathering information on user behavior, IP addresses and so on.
- Traffic interception: In more malicious cases, hijackers can actively intercept and manipulate data while it passes through their network. This could lead to data breaches, unauthorized access to confidential information, intellectual property theft, or tampering with the data in transit.
- Redirection to malicious websites: Hijackers can use BGP hijacking to redirect traffic to malicious websites, which may host malware or phishing pages. This can lead to users unknowingly downloading harmful software or giving away sensitive information like login credentials.
- Spoofing: BGP hijacking can also be used to spoof IP addresses to mask the true origin of malicious traffic. This technique is sometimes used by spammers and organizers of DDoS attacks.
Each of these consequences highlights the critical need for robust security measures to mitigate the risks posed by BGP hijacking. Without proper protections in place, organizations risk severe operational, financial, and reputational damage.
