Exploring BGP: What It Is and How It Works
Border Gateway Protocol (BGP) is the routing protocol for the Internet. BGP is used to exchange routing information between the individual networks that make up the Internet. Essentially, BGP is what allows the Internet to function as a vast, interconnected network of networks by establishing the most efficient path from one location to another across multiple networks.
Think of BGP as the Internet’s ZIP-code system, built on top of the IP addressing system. It directs data through the most efficient routes across networks, constantly adjusting to find the best path based on current conditions.
How Does BGP Work
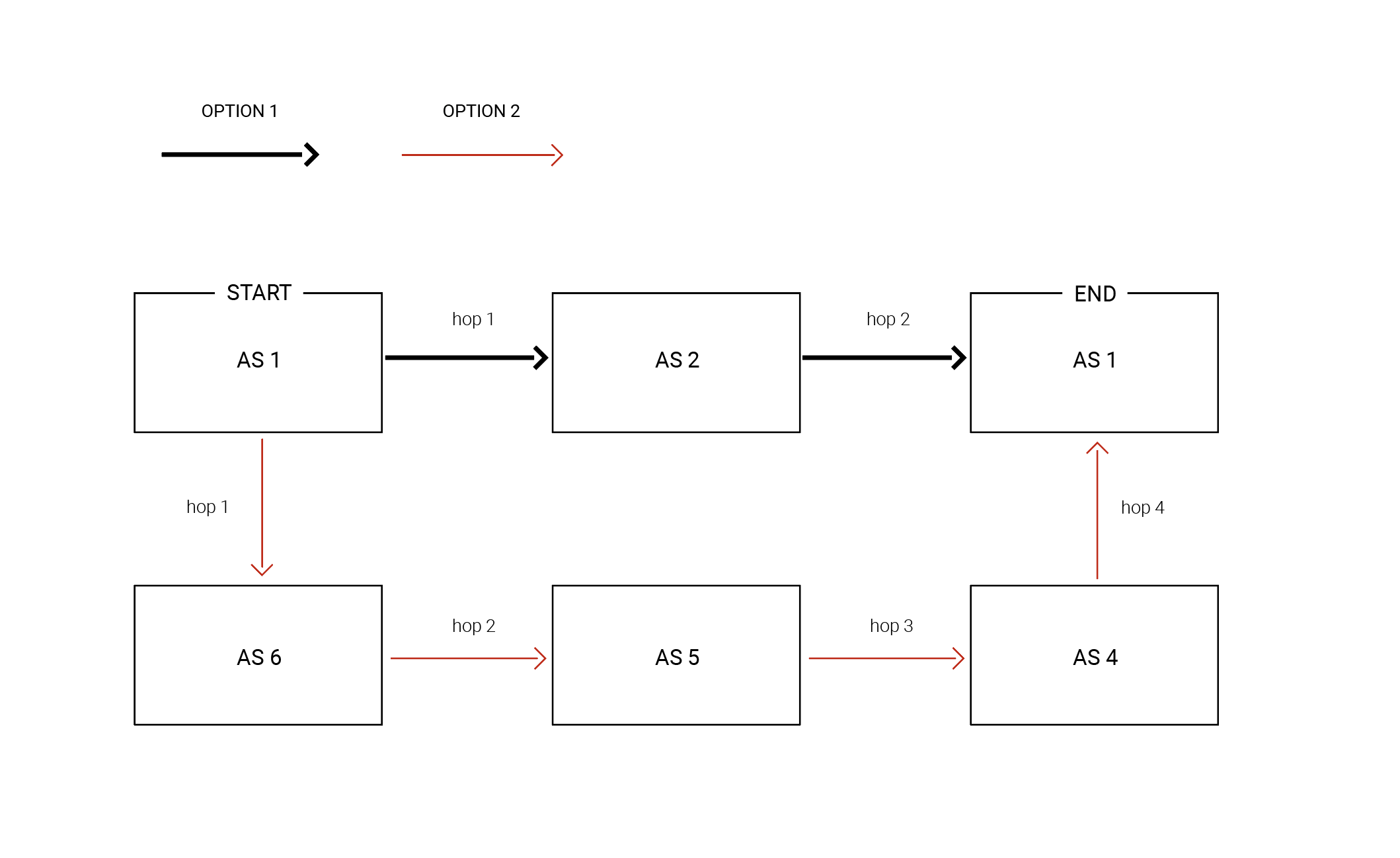
As mentioned earlier, the purpose of BGP is to establish the most efficient path for data to travel from one AS to another. With tens of thousands of autonomous systems worldwide, interconnected in a complex, mesh-like structure, finding the optimal route can be quite challenging.
To accomplish this, BGP relies on several key mechanisms:
- BGP Route Advertisement: Each AS shares information about the IP prefixes it can reach with its neighboring ASes. This information helps build a map of routing paths across the global network.
- BGP Best Path Selection: When multiple paths to the same destination are available, a BGP router uses a list of criteria to select the best one. Factors such as the number of AS hops, cost of transmission, and path reliability are considered to determine the most efficient route.
- BGP Routing Tables: BGP routers store the best paths in their routing tables, which are then used to direct data packets through the network. These tables are constantly updated as new routes are advertised or as network conditions change.
The Internet is a dynamic environment, with routes frequently becoming available or unavailable. BGP routers continuously monitor these changes and update their routing tables accordingly, ensuring that data always travels along the most optimal path.
What is the Difference Between Internal BGP and External BGP
BGP can be used both for exchanging Internet routes between different autonomous systems and for exchanging them within a single AS. Therefore, BGP comes in two flavors:
- eBGP (External or Exterior Border Gateway Protocol): Used for communication between routers in different autonomous systems, exchanging information to facilitate data transfer across the internet.
- iBGP (Internal or Interior Border Gateway Protocol): Used for sharing external routing information between routers within a single autonomous system (AS).
iBGP should not be confused with IGP (Interior Gateway Protocol), a category of routing protocols used for distributing internal routing information within an autonomous system.
Challenges and Vulnerabilities of BG
Originally devised in 1989 and famously drafted on the back of “three ketchup-stained napkins,” the Border Gateway Protocol (BGP) has become the backbone of the Internet. The problem is, at the time of its creation, security was often not taken into account, and many systems on the Internet were built to automatically trust users. BGP was no exception.
The protocol is designed so that routers running BGP accept advertised routes from other BGP routers by default. On one hand, this enables automatic and decentralized routing of traffic across the Internet. On the other hand, it makes BGP vulnerable to accidental or malicious disruptions, known as BGP route leaks and BGP hijacking.
- BGP route leaks occur when an autonomous system advertises routes to other ASes that it should not be advertising. This often happens due to a misconfiguration, where routes intended for internal use or specific partners are made public. While typically unintentional, BGP leaks can lead to significant issues such as inefficient routing, increased latency, and, in some cases, traffic being routed through insecure paths.
- BGP hijacking is an illegitimate prefix announcement by a malicious or misconfigured autonomous system (AS) that results in the redirection of traffic. For example, a malicious actor can use BGP hijacking to force traffic to pass through a network under their control. Whether intentional or not, BGP hijacking can cause serious issues, such as traffic interception, data loss, and service disruption.
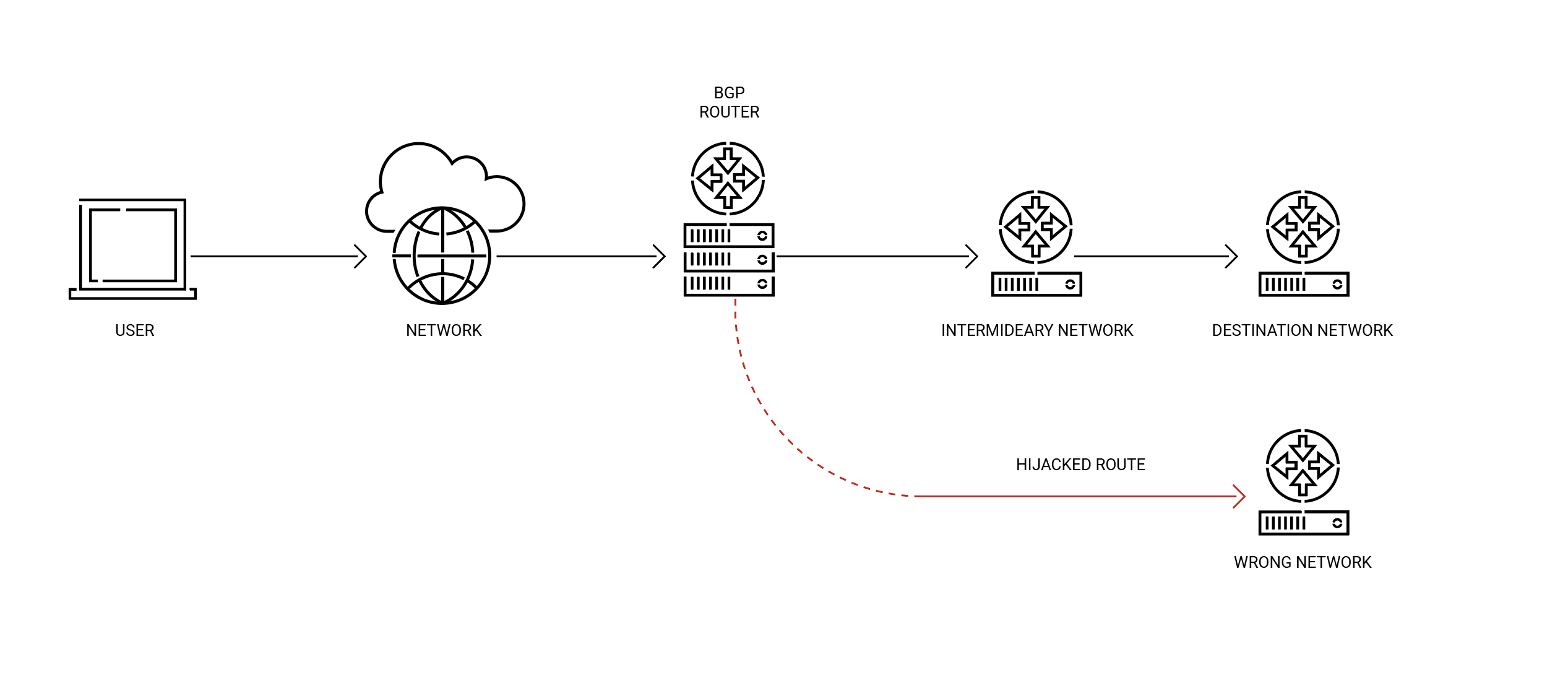
These incidents occur frequently, with the root cause being that BGP is built on trust: ASes trust the route information they receive from their peers. As a result, when a peer announces incorrect route information, whether intentionally or accidentally, traffic can be misdirected to unintended destinations, sometimes with dangerous consequences.
Securing Border Gateway Protoco
Over the decades, various BGP security measures have been introduced to enhance protocol’s reliability, including BGP route filtering, BGP neighbor authentication, and more. Among these, the most significant advancements are RPKI and ROA, which have already had a substantial positive impact on BGP security.
- RPKI (Resource Public Key Infrastructure) is a cryptographic framework designed to secure the BGP routing infrastructure by allowing network owners to validate route updates and ensure that routing announcements are legitimate. This framework helps prevent BGP hijacking and BGP route leaks.
- ROA (Route Origin Authorization) is a key component of RPKI — a digitally signed object that specifies which AS is authorized to originate a specific IP prefix. When a BGP route announcement is made, other ASes can check the ROA to verify that the announcement is legitimate. If the route does not match a valid ROA, it can be flagged as potentially fraudulent, helping to prevent BGP hijacking.
However, while RPKI and ROA have proven effective in enhancing BGP security and their adoption is steadily increasing, they have not yet been implemented across the entire internet. As a result, BGP vulnerabilities still exist, and global Internet traffic remains at risk. Therefore, it is crucial for network engineers to continuously monitor for BGP incidents to promptly address any arising issues.
The right tool for this task is Qrator.Radar, one of the world’s largest real-time routing data collectors and network behavior anomaly detectors. With its comprehensive insights and alerts on BGP-related issues, Qrator.Radar helps maintain a secure, reliable, and resilient network infrastructure, protecting against BGP hijacking and other routing-related threats.