
Starting in Q1 2024, we modified our methodology to better account for the growth in channel capacity and attack volume. We now filter out all incidents with an intensity of less than 1 Gbps, considering these minor attacks as "white noise." This adjustment helps us focus on the most significant events.
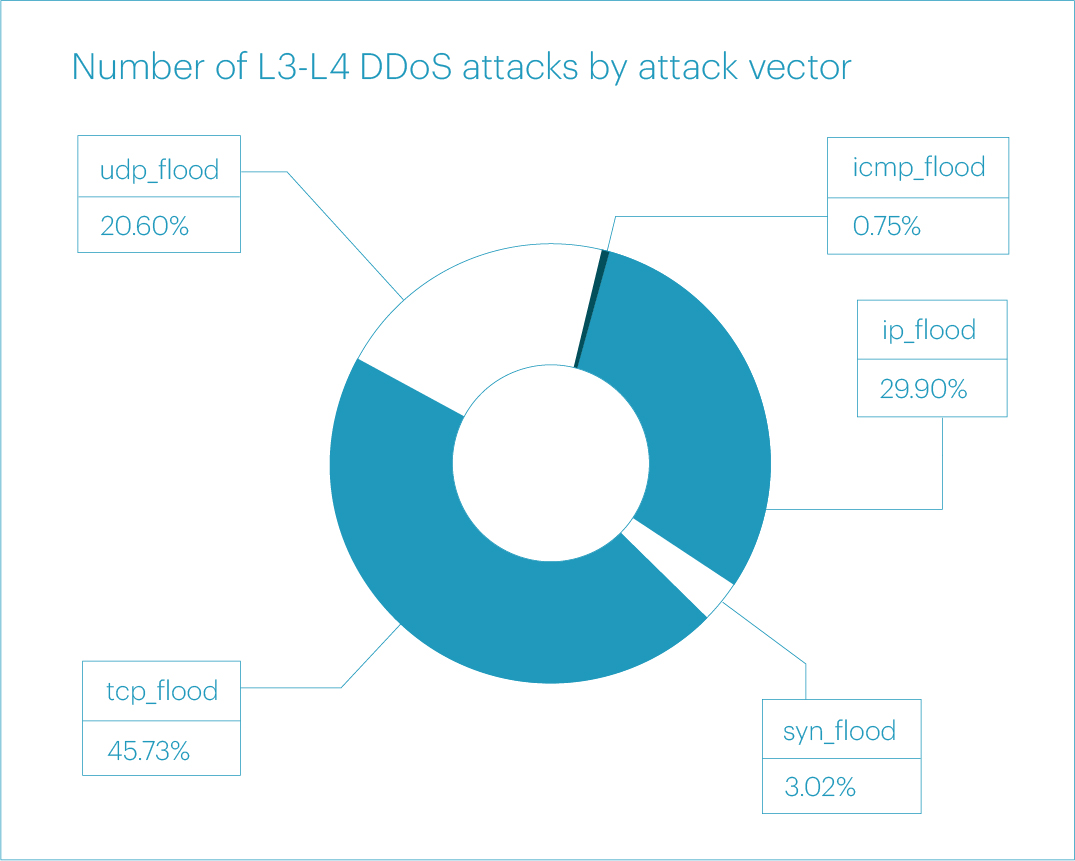
In the second quarter of 2024, the distribution of attacks by vector shifted significantly compared to the first quarter. Single-vector TCP flood attacks dominated, accounting for nearly half of all L3-L4 attacks at 48.91%. The IP fragmentation flood came in second, representing 22.43% of attacks. In third place was the UDP flood, which accounted for 9.66% of attacks.
In fourth place were multi-vector attacks combining UDP and IP fragmentation floods, with a share of 9.35%. Finally, fifth place was occupied by multi-vector attacks combining UDP, TCP, and IP fragmentation floods, making up 2.49% of attacks.
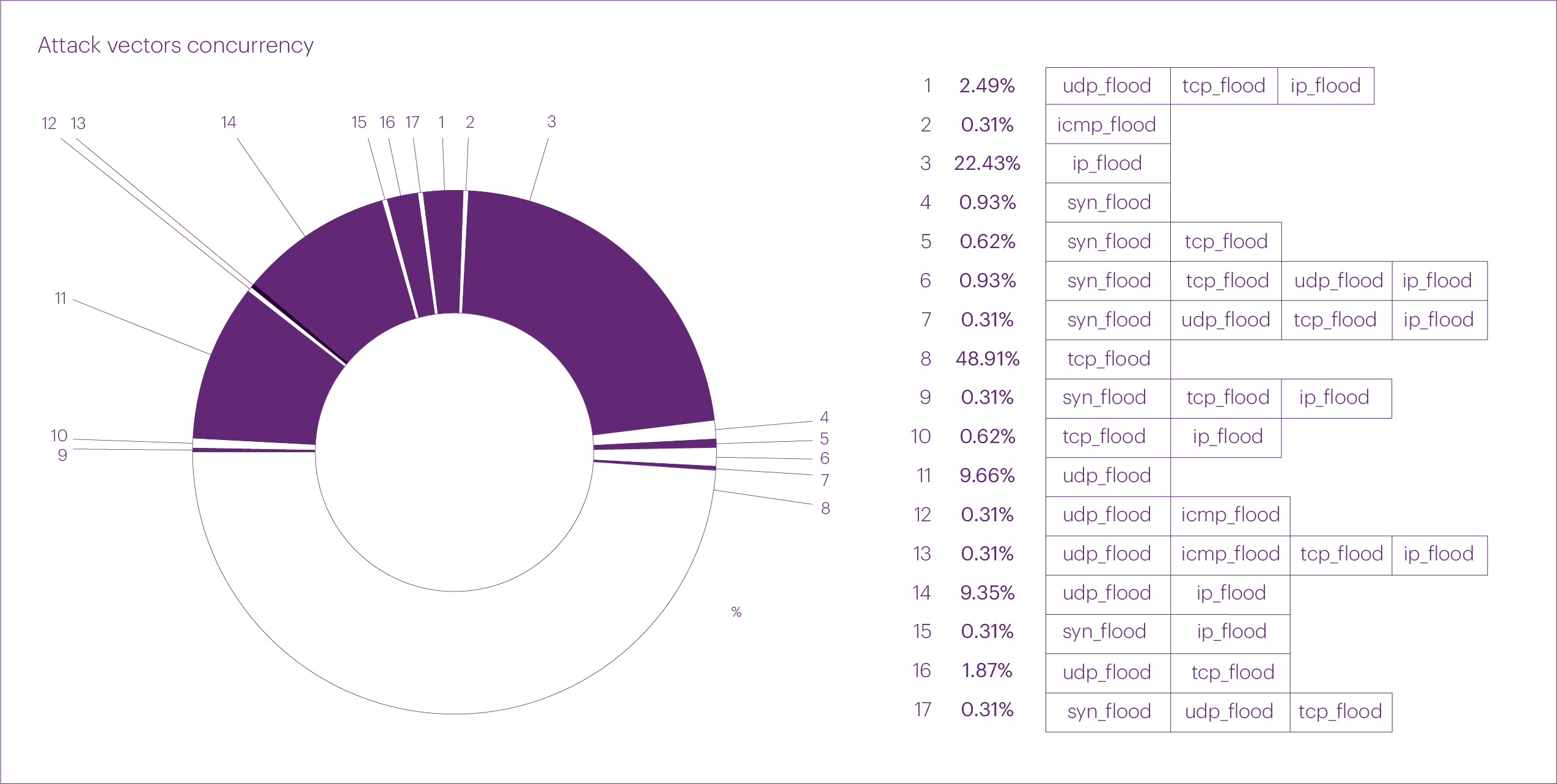
The overall share of multi-vector attacks in the second quarter was 17.76%, slightly lower than in the first quarter but still significantly higher than in 2023. We attribute this increase to the rise in attackers' capabilities, which allows them to organize a large number of multi-vector attacks.
Multi-vector attacks are especially challenging to detect and mitigate, making them more likely to succeed, particularly against unprotected or partially protected infrastructures. This effectiveness contributes to their growing popularity among attackers.
Regarding pure attack vectors, the distribution in the second quarter was as follows:
After the extremely high figures observed in the previous reporting period, the duration of attacks in this quarter fell even below the 2023 level. On average, attacks in Q2 2024 lasted only 40 minutes. When excluding peak indicators (i.e., at the 90th percentile), the duration was just 12.5 minutes.
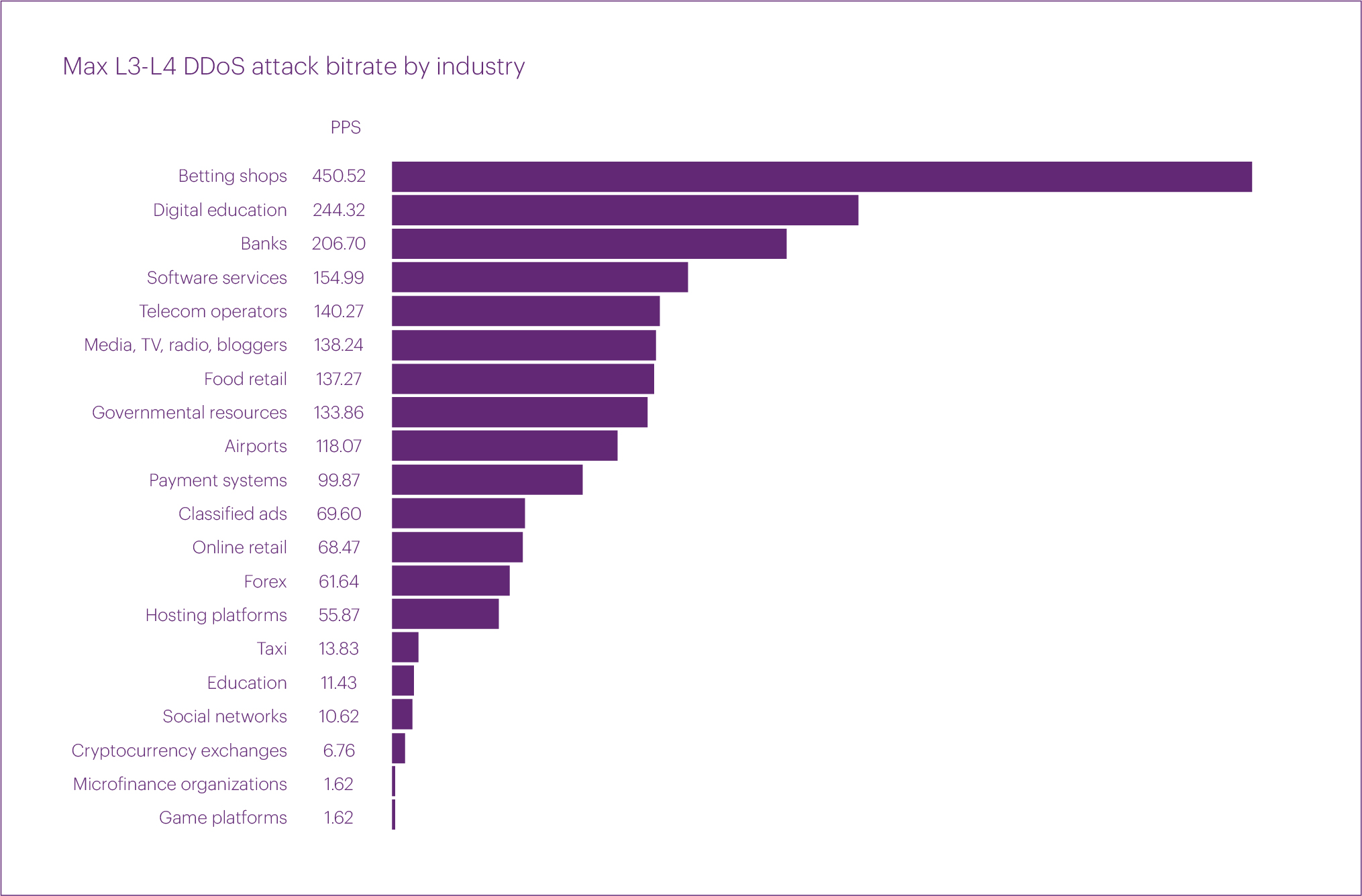
Regarding the intensity of L3-L4 attacks, after several quarters of increased activity, there was a cutback, returning to a level slightly above that of the second quarter of last year. The maximum bitrate was observed during a TCP flood attack on the Betting shops segment, reaching 450.52 Gbps. We believe that this attack was linked to the Euro 2024.
The second place goes to an IP fragmentation flood attack on the Digital education segment, which peaked at 244.32 Gbps. The full statistics of attack throughput by various vectors are as follows:
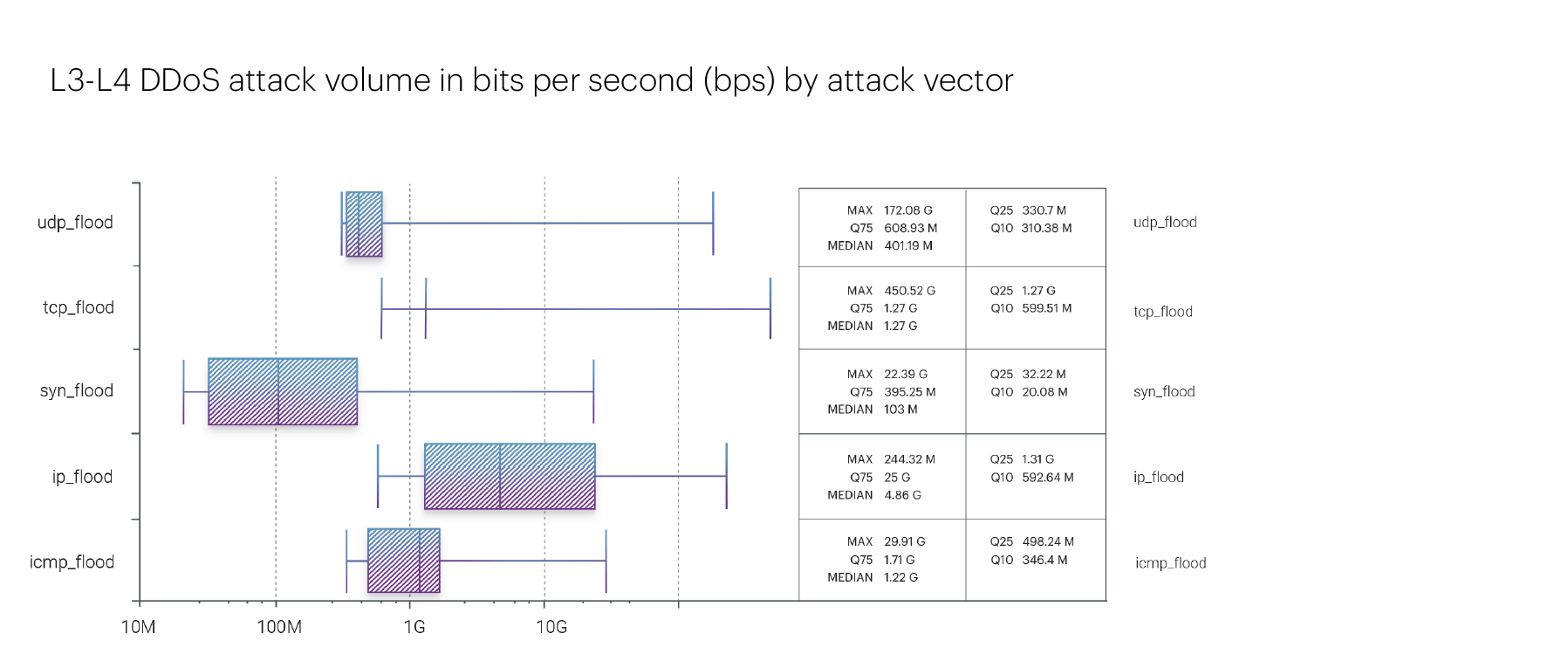
Reviewing historical data from 2021 to 2024, the second quarters are typically marked by a slight decrease in the peak intensity of attacks, a trend that has been particularly noticeable in the last two years. Interestingly, TCP flood attacks have been the most prevalent during the second quarters for three consecutive years, whereas UDP flood attacks are more common in other periods.
2021 Q2: peak volume 574.71 Gbps — IP fragmented flood
2022 Q2: peak volume 520.18 Gbps — TCP flood
2023 Q2: peak volume 333.78 Gbps — TCP flood
2024 Q2: peak volume 450.52 Gbps — TCP flood
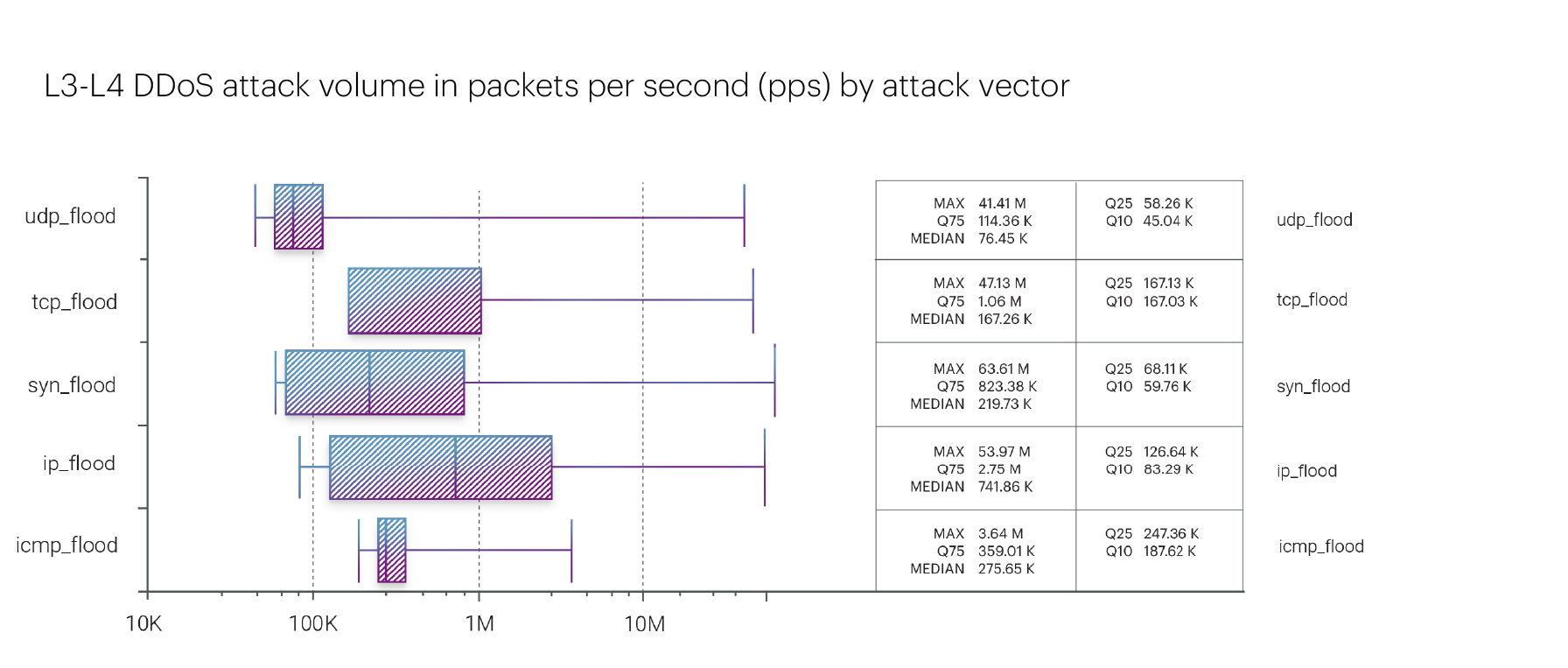
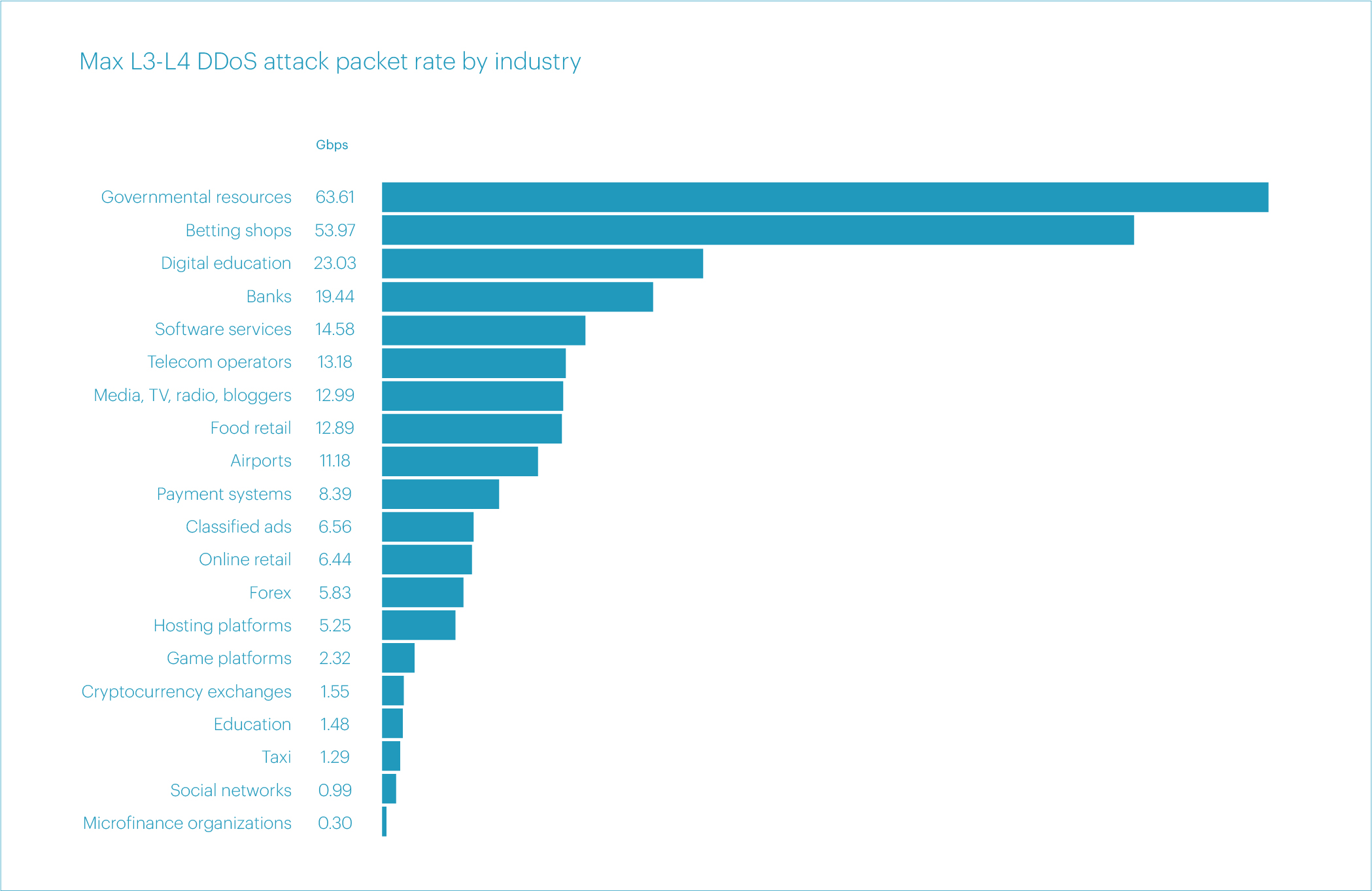
Regarding the packet rate, the distribution of maximum attack intensities is significantly different. In Q2 2024, the highest packet rate was recorded for a SYN flood attack, reaching 63.61 Mpps. This was followed by an IP fragmentation flood at 53.97 Mpps and a TCP flood at 47.13 Mpps.
The largest number of attacks in Q2 2024 targeted the FinTech (25.35%), E-commerce (17.01%), and IT&Telecom (13.89%) macro segments.
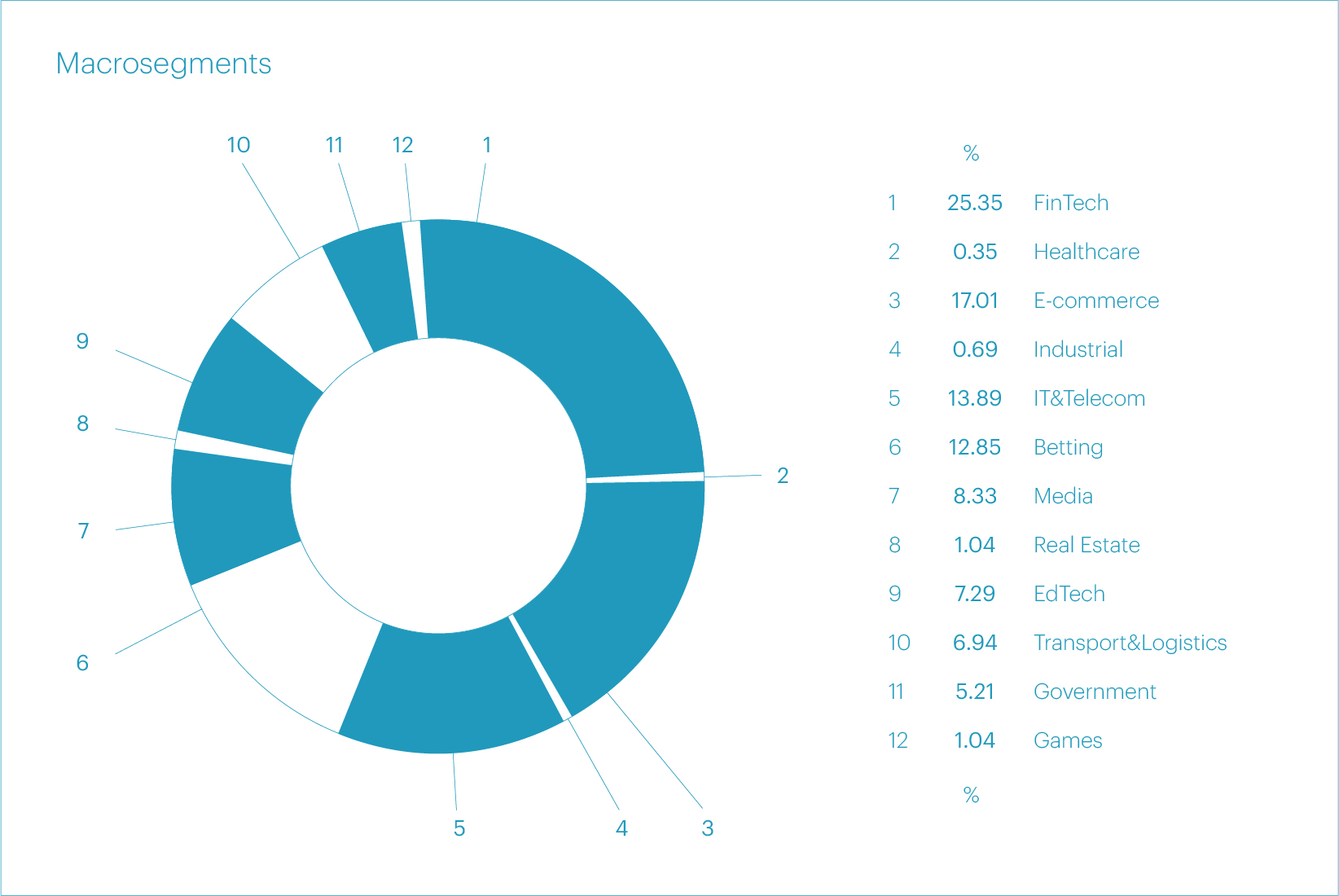
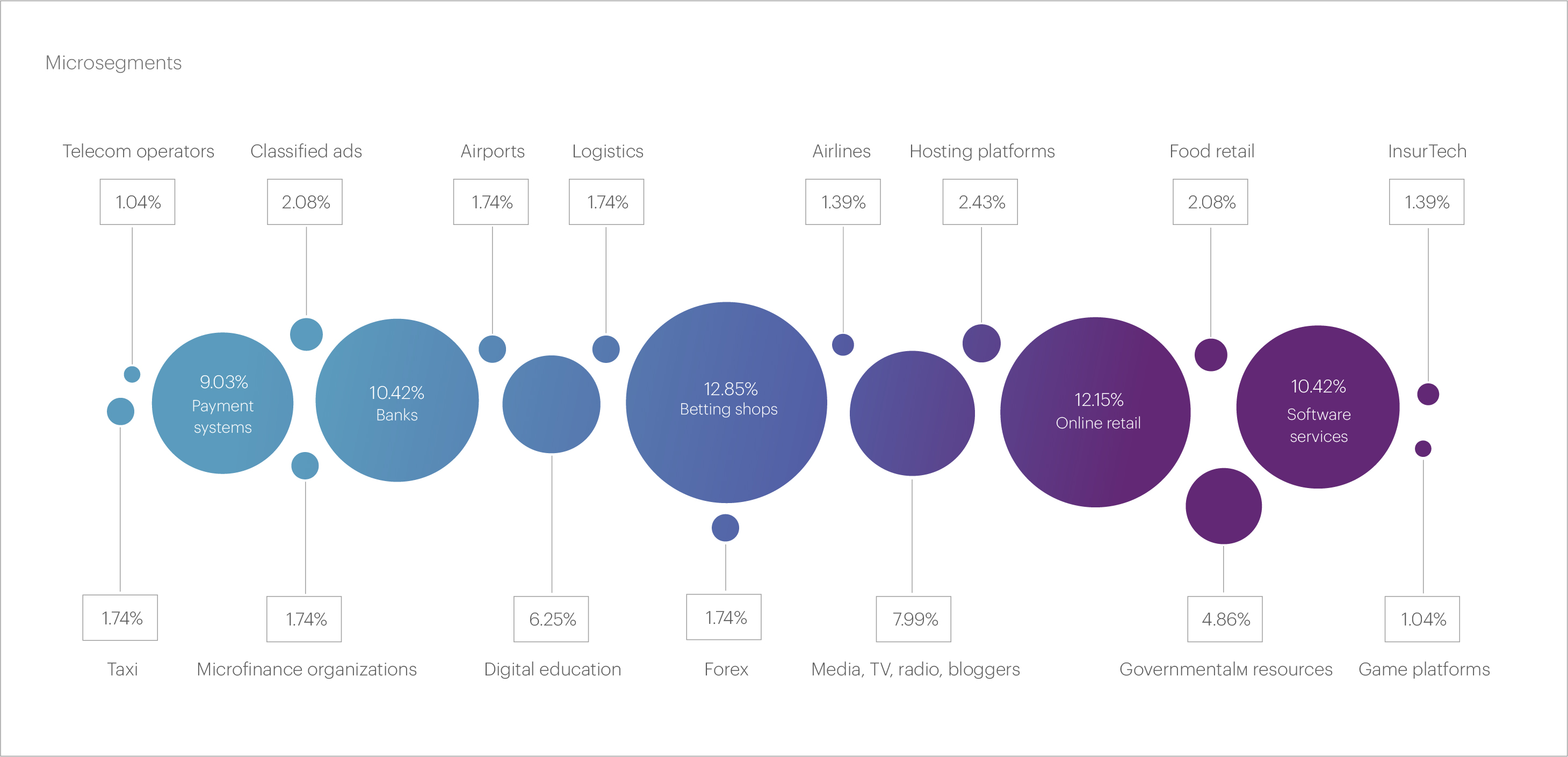
Regarding the micro segments that were most frequently attacked in Q2 2024, the top five are as follows: Betting shops (12.85%), Online retail (12.15%), Banks (10.42%), Software services (10.42%), and Payment systems (9.03%). We link the high number of L3-L4 attacks on the Betting shops segment to the European Football Championship.
As we mentioned earlier, no records were set in the second quarter for the duration of L3-L4 attacks. The longest continuous attack targeted the Media, TV, radio, bloggers segment, lasting 13.01 hours. The second longest was an attack on the Payment systems segment, which continued for 7.08 hours. The third longest incident occurred in the Betting shops segment, lasting just 1.01 hours.
The attacks with the highest intensity in Q2 2024 targeted the Betting shops (450.52 Gbps), Digital education (244.32 Gbps), and Banks (206.7 Gbps) segments. Although no new records were set here either, it is worth noting the increase in the number of attacks with a bitrate of over 100 Gbps. While in Q1 such attacks affected seven micro-segments, in Q2 they impacted nine: in addition to the three leaders mentioned above, these included Software services, Telecom operators, Media, Food retail, Government resources, and Airports. The Payment systems micro segment came in tenth with an intensity of 99.87 Gbps, just a bit below 100.
When it comes to the maximum packet rate, the rankings are quite surprising. The Government resources segment leads with 63.61 Mpps. The Betting shops segment follows in second place with 53.97 Mpps, and the Digital education segment comes in third with 23.03 Mpps.
The largest botnet we observed in Q2 was slightly larger than the Q1 record, consisting of 60,500 devices compared to 51,400 devices in the previous quarter.

This botnet was utilized during an attack on the Banks segment that occurred on May 25. The devices in the botnet were located in eight countries: the United Kingdom, the United States, Romania, Poland, Austria, Brazil, Canada, and France.
In Q2 2024, the number of application layer (L7) DDoS attacks decreased by about a quarter compared to the same quarter last year, continuing the trend discussed in the previous quarterly report.
The top three most popular attack classes have remained unchanged for the fourth consecutive quarter. Leading the pack with the largest share (32.79%) are Request Rate Patterns attacks, characterized by request frequencies that deviate from the expected behavior of legitimate users. In second place (25.71%) are attacks involving an unusual set of request headers, which we classify as Rotating Client Secondary Attributes. Finally, in third place are multi-class (Multiple Matching Criteria) attacks, accounting for 14.0% of the total.

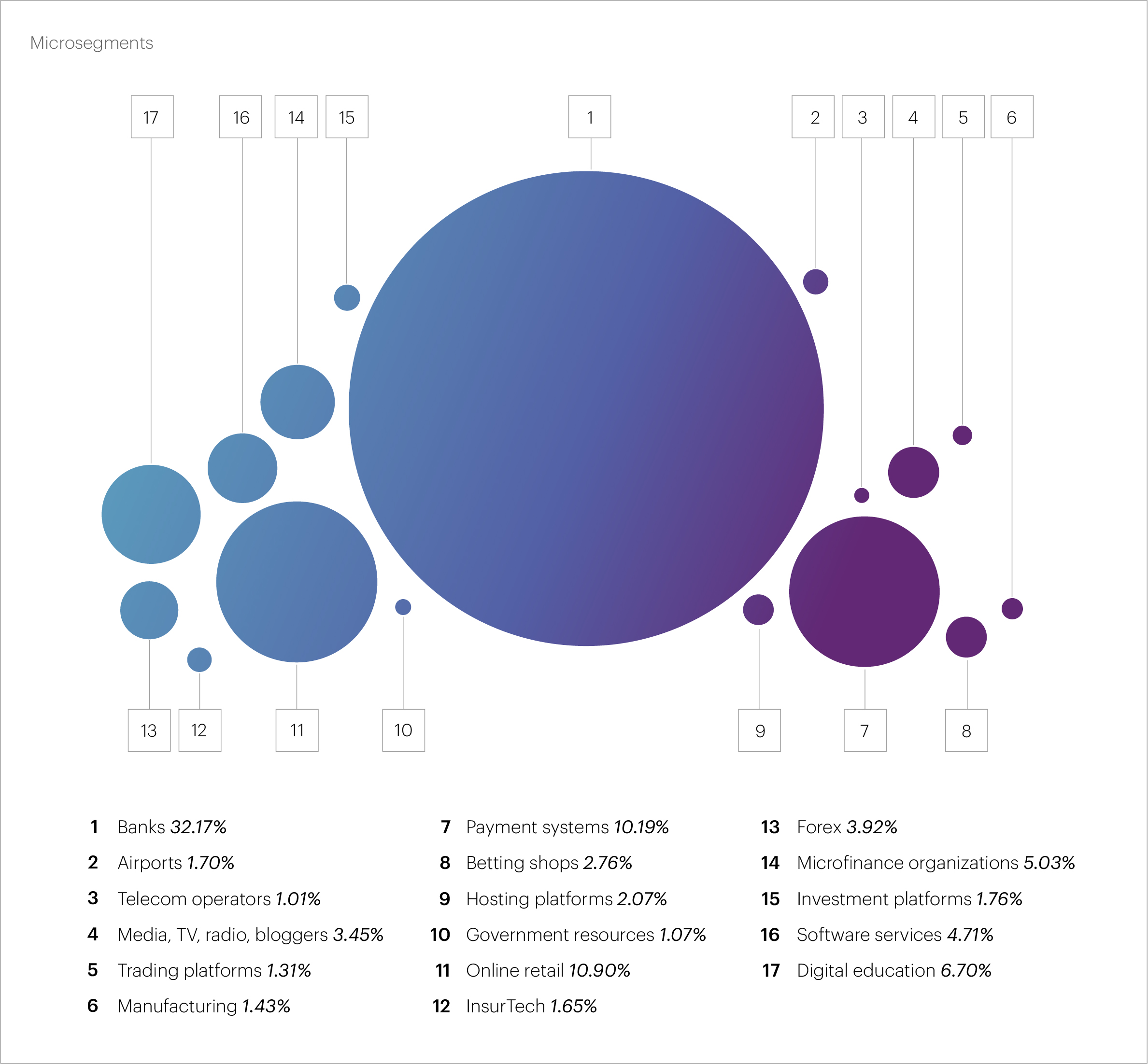
The FinTech macro segment stands out among the attacked industries, with its share steadily growing for five consecutive quarters. For the second quarter in a row, FinTech has accounted for more than half of all L7 DDoS attacks, reaching 56.8% in Q2 2024. Within the financial sector, the most frequently attacked organizations are banks, which make up 32.17% of the total attacks, followed by payment systems at 10.17% and microfinance organizations at 5.03%.
The E-commerce macro segment occupies second place in terms of the number of attacks. Notably, its share has been decreasing for the third consecutive quarter. While in Q2 2023 this was the most attacked segment, comprising a third of all L7 attacks, it now accounts for a mere 13.84%. The IT&Telecom segment is in third place with 7.79%, its share also decreasing for the fourth consecutive quarter.
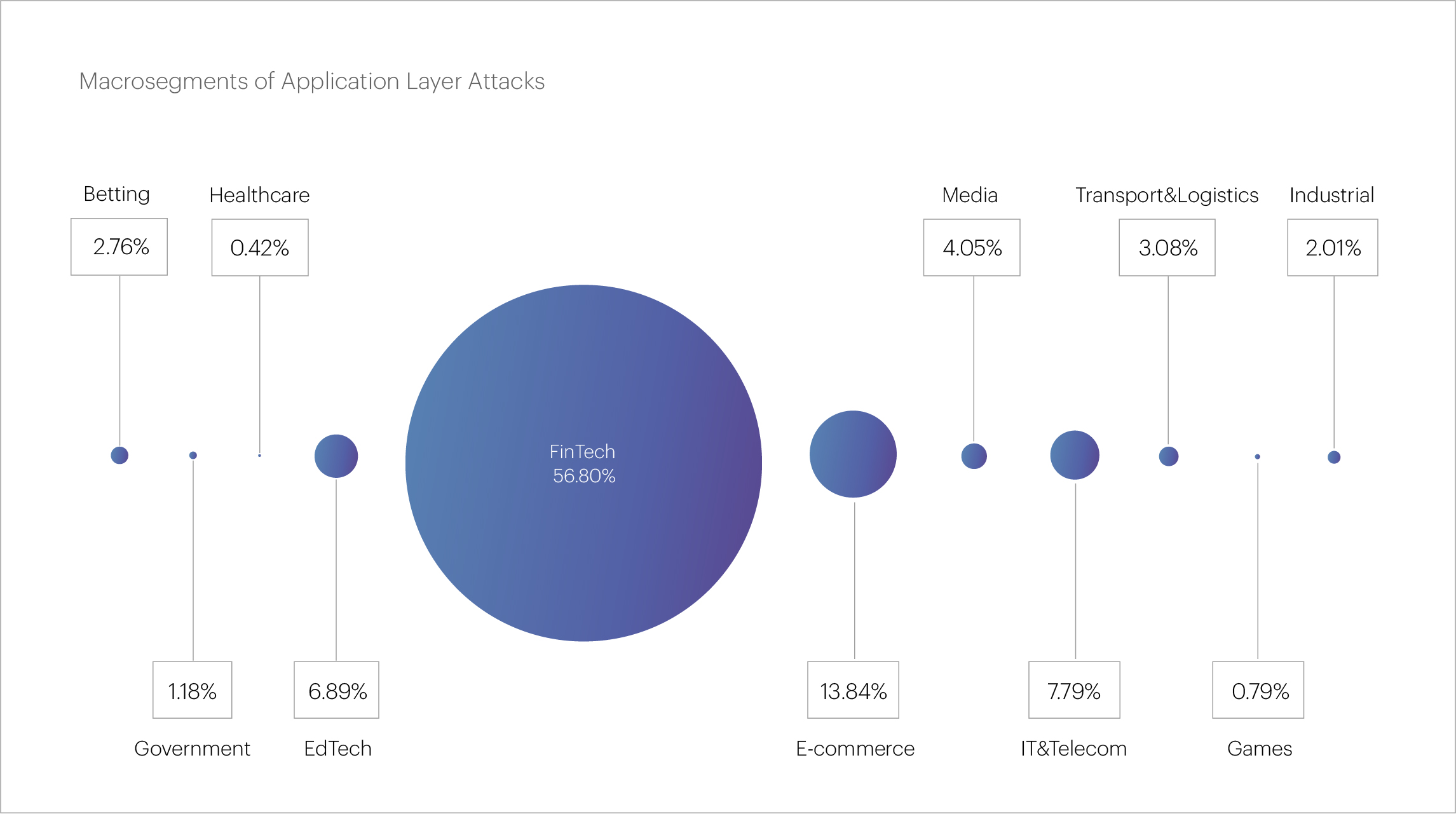
The "hot five" of micro segments that most often become victims of application layer attacks looks like this: Banks are ahead by a wide margin (32.17%), followed by Online retail (10.9%) and Payment systems (10.17%). Digital education (6.7%) and Microfinance organizations (5.03%) round out the top five.
While the quantity of L7 attacks in Q2 2024 noticeably decreased, their quality increased significantly. For example, there were two attacks that lasted more than two days, both occurring in April. The first attack targeted the Telecom operators segment and continued for over 49 hours. The second attack targeted Payment systems and kept going for a little over 48 hours.
The same applies to the intensity of attacks — in Q2, there was a significant number of application layer attacks with high RPS. Interestingly, all five attacks with the highest peak RPS targeted the Betting shops segment:
The most powerful attack peaked at 1.56 million RPS and lasted 34.5 minutes
The second attack had a peak of 677 thousand RPS and continued for only 2.5 minutes.
The third attack occurred a day after the second, with very similar characteristics: 645 thousand RPS and a duration of 2.5 minutes.On the same day, the forth attack occurred peaking at 424 thousand RPS and continuing for 42.5 minutes.
Finally, the fifth attack had a peak of 302 thousand RPS and lasted 18 minutes.
In addition, there were six more attacks in the second quarter with a peak RPS above 200 thousand — four targeting the Banks segment and two more targeting the Betting shops segment. As in previous cases, we associate this surge in activity in the Betting shops segment with the 2024 European Football Championship.
The maximum number of devices involved in a single L7 DDoS attack in Q2 2024 was 286,622; this attack targeted the Banks segment.
In Q2 2024, for the first time in several quarters, we observed changes in the top three countries representing the main sources of malicious traffic. Russia still ranks first, accounting for 22.03% of all blocked IP addresses. The United States has taken second place with 18.32%, a significant increase compared to previous periods.
This quarter, Brazil, with a share of 4.79%, took third place, a position previously held by China for an extended period. However, in Q2 2024, China’s share dropped sharply to 2.23%, relegating it to 10th place.
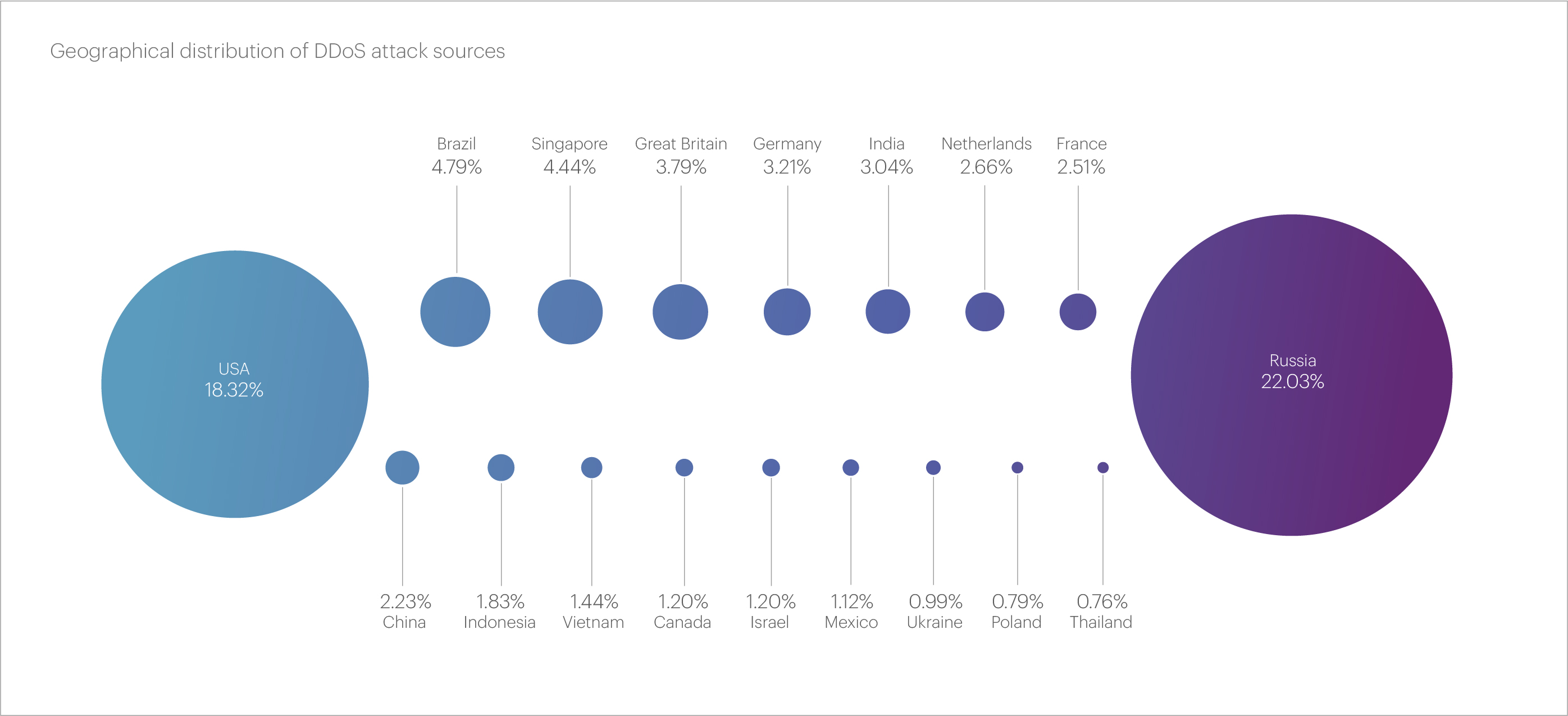
Among the countries that entered the top-10, Singapore (4.44%) and the United Kingdom (3.79%) significantly increased their shares. Conversely, Germany's share notably decreased to 3.21%. The top-10 is rounded out by countries whose shares remained approximately at the level of the previous quarter: India (3.04%), the Netherlands (2.66%), and France (2.51%).
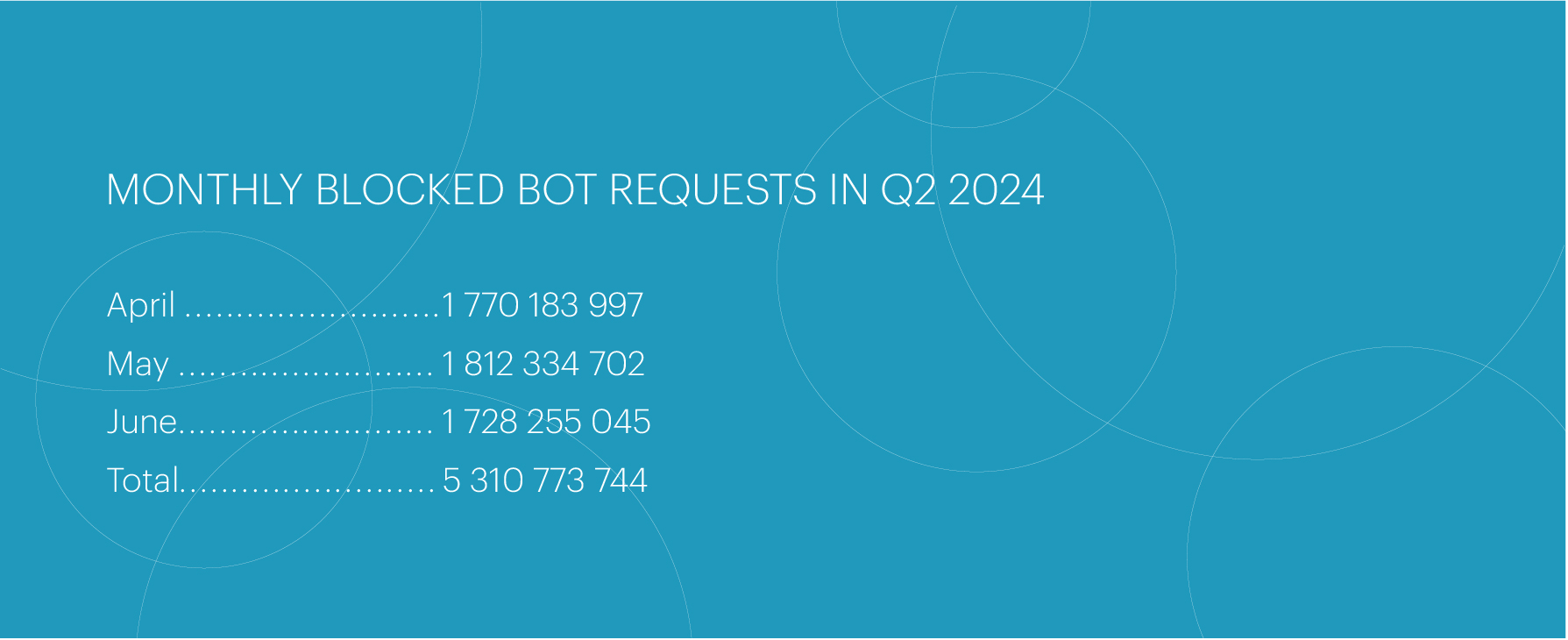
In Q2 2024, we did not observe a significant increase in bot attacks compared to Q1. The number of blocked bot requests increased by approximately 5%, totaling at 5,310,773,744. The highest number of attacks was recorded in May; however, overall activity for this quarter was evenly distributed across the months.
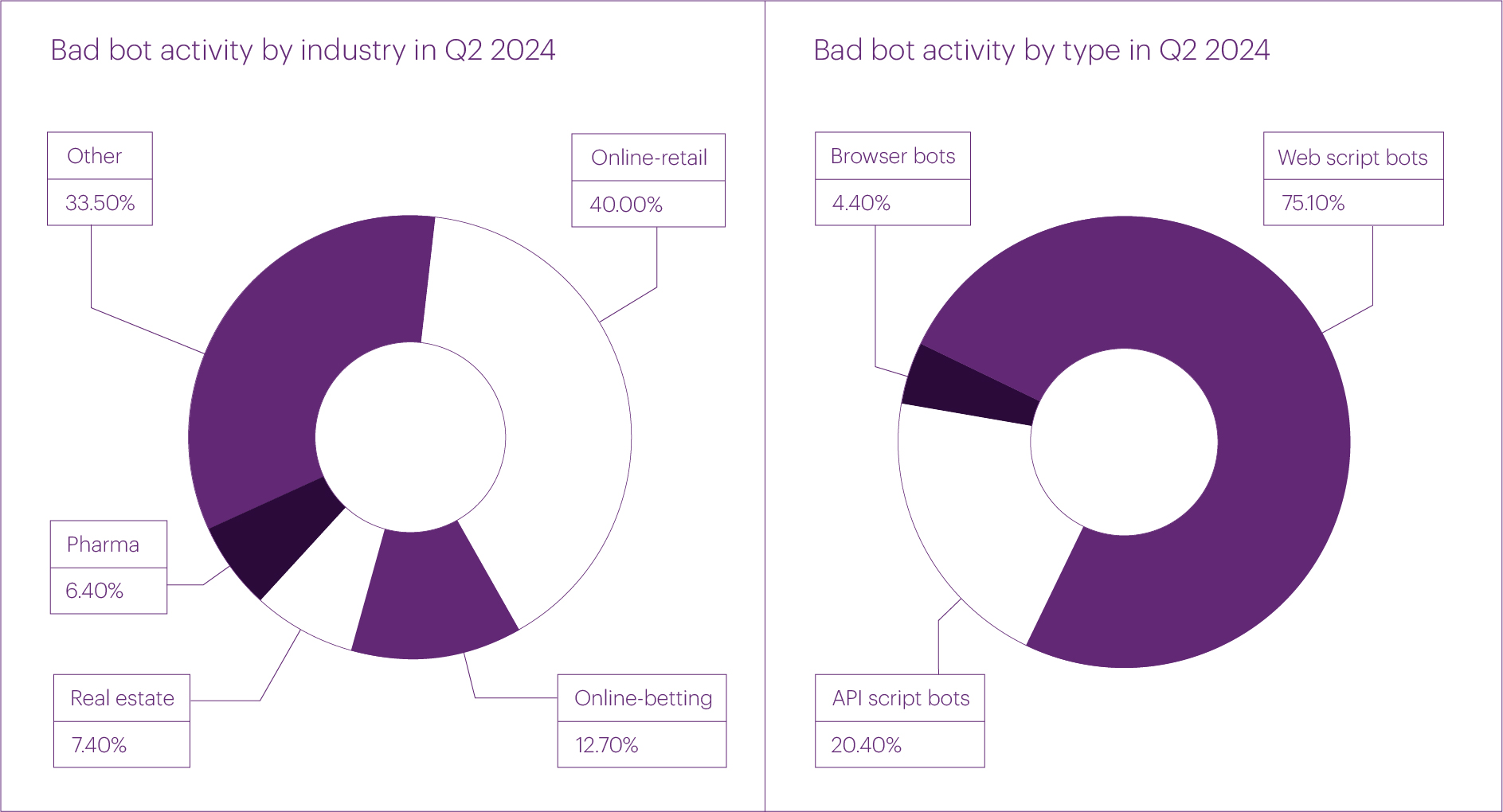
In the second quarter, the industry segments most frequently attacked by bots were as follows: Online retail accounted for 40% of all bot activity, and Online betting for 12.7%. The Banks segment fell out of the top due to a continued decline in its share. Significant bot activity was also observed in the Real estate (7.4%) and Pharmacies (6.4%) segments.
The largest bot attack of the second quarter occurred on May 29 and targeted the Logistics segment. A total of 20,021,633 requests were blocked during this attack, which is approximately 10% less than the record set in the previous quarter.
The fastest attack of the quarter also occurred on May 29, targeting Online Retail. It reached 17,500 requests per second at its peak, which is 75% less than the record set in the previous period.
In terms of the distribution of bot attacks by type, the vast majority of requests in Q2 were directed at web pages. The share of such activity has increased sharply compared to previous periods, reaching 75%. We suspect that this may be related to the collection of data for training AI models.
To sum it up, bot activity in Q2 2024 was high but stable, without any major spikes. Notably, we did not observe any highly intensive bot attacks (i.e., with a number of requests per second of 20,000 or more) during this period.
We predict even more intensive activity in the Online retail segment in Q3, related to the sales season.

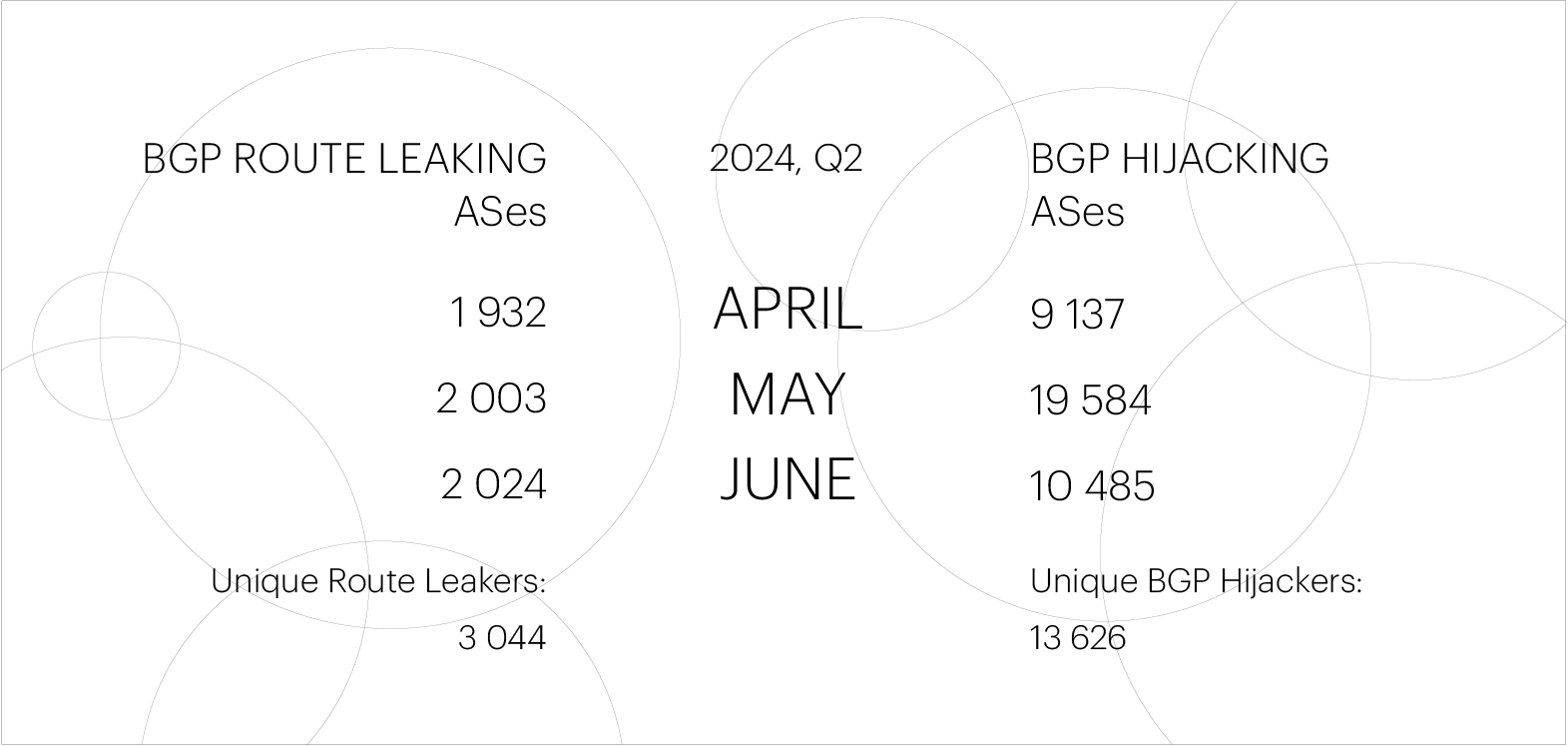
The number of unique autonomous systems (ASes) that perpetrated BGP Route Leaks in Q2 2024 remained virtually unchanged from Q1: 3,044 (versus 3,017 in the previous quarter).
At the same time, the number of unique ASes that perpetrated BGP Hijacks decreased slightly: from 15,000 in Q1 to 13,626 in Q2.
One of the possible causes of BGP route leaks is the restructuring of network architectures, such as during the acquisition of organizations. It's worth mentioning that such incidents can occur both intentionally (a specific, possibly temporary network configuration used during the restructuring) and accidentally, due to network engineers' mistakes.
As we have repeatedly noted, the decrease is mainly due to the widespread implementation of RPKI ROA-based validation.
The Qrator.Radar team has established specific thresholds to distinguish global incidents from all other events. These thresholds include the number of affected prefixes, the number of autonomous systems involved, and the extent to which the anomaly is distributed across routing tables.
The number of global BGP route leaks in the second quarter decreased by half compared to the first quarter, dropping from 12 to 6.
As for global BGP hijacking, there was only one incident in the second quarter, which occurred on May 25. Notably, we didn't register any global BGP incidents at all in April.
| Global BGP Route Leaks | Global BGP Hijacks | |
| 0 | April | 0 |
| 2 | May | 1 |
| 4 | June | 1 |
A particularly noteworthy incident of Q2 2024 was a major BGP route leak that took place on May 24, just a day before the mentioned BGP hijack. This leak was caused by the Brazilian provider Megatelecom and led to 5,333 conflicts involving 593 ASes from 68 countries.The leak resulted from the merging of network infrastructures during Megatelecom's acquisition of another Brazilian provider, InterNexa Brasil.


Share your experience and expectations regarding DDoS protection. Your answers will help us tailor solutions to meet your cybersecurity needs.
Tell us about your company’s infrastructure and critical systems. This will help us understand the scope of protection you require.
Help us learn about how decisions are made in your company. This information will guide us in offering the most relevant solutions.
Let us know what drives your choices when it comes to DDoS protection. Your input will help us focus on what matters most to you.