A few days ago several cybersecurity resources reported details of an entirely malicious traffic redirection that combined DNS, and BGP hijacking. The primary goal of this attack was to steal money from different cryptocurrency wallets and services. Moreover, it was successful, since Amazon did not detect it in time. Today, on April 26, another significant incident happened that seems to be also unnoticed by the majority of players.
An AS267286, registered almost two years ago, stayed invisible until the event we are going to cover below when it announced 28 prefixes to the outer world. Among those 28 separate announcements sixteen were /8 prefixes (6,25% of IPv4 address space). This initial announcement was accepted by ASNs that belong to China Telecom (AS4134, AS4809), which in its turn propagated it to Tier1 carriers and thus helped to spread it all over the world.
A spread of /8 prefixes on their own does not always affect end-user services or applications. To redirect traffic using /8 prefix, several conditions are necessary:
With high probability, we can state that those /8 prefixes were distributed at São Paulo IX, the biggest IX in Brazil. Furthermore, several other networks were affected, of the size ranging from /24 and up to /16, belonging to several companies, including Equinix and Incapsula. There were already 5 waves with the same set of prefixes:
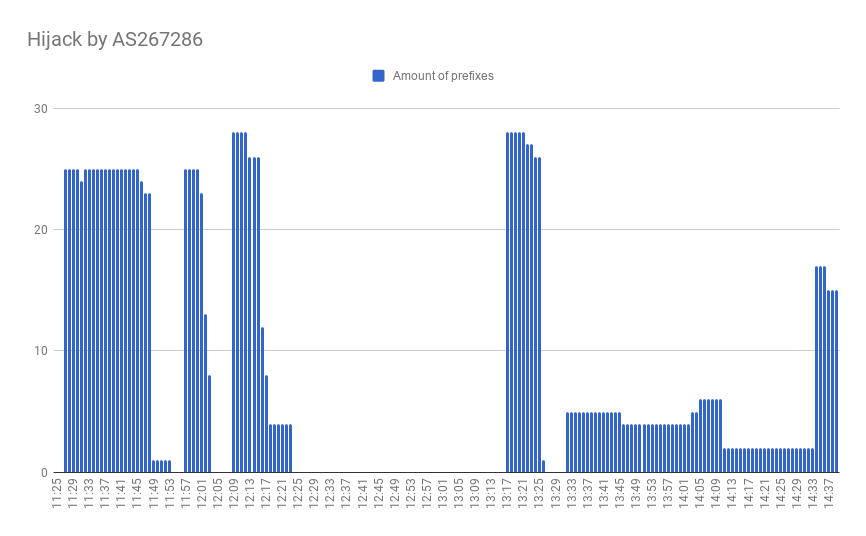
These particular announcements and their consequences show us that the quality of networks in several developing and growing regions is often sacrificed in favor of their growth speed. It also indicates the absence of proper filters between the China Telecom network and its connections with customers. Thus the absence of filters between peers (in this case between China Telecom and Tier1 carriers) made this anomaly global.
Is that just someone’s mistake or again a malicious BGP hijack? It is hard to tell without details from affected networks and services within. What we can say for sure for now - this is 100% illegitimate.


Share your experience and expectations regarding DDoS protection. Your answers will help us tailor solutions to meet your cybersecurity needs.
Tell us about your company’s infrastructure and critical systems. This will help us understand the scope of protection you require.
Help us learn about how decisions are made in your company. This information will guide us in offering the most relevant solutions.
Let us know what drives your choices when it comes to DDoS protection. Your input will help us focus on what matters most to you.